Guest
Guest
 |  Subject: documents demonstrating the extent to which the CIA uses backdoors to hack smartphones, computer operating systems, messenger applications and internet-connected televisions Subject: documents demonstrating the extent to which the CIA uses backdoors to hack smartphones, computer operating systems, messenger applications and internet-connected televisions  Tue Mar 07, 2017 5:12 pm Tue Mar 07, 2017 5:12 pm | |
| http://www.blacklistednews.com/Snowden%3A_What_The_Wikileaks_Revelations_Show_Is_"Reckless_Beyond_Words"/57208/0/38/38/Y/M.html [size=35]SNOWDEN: WHAT THE WIKILEAKS REVELATIONS SHOW IS "RECKLESS BEYOND WORDS"[/size] Published: March 7, 2017
[url=https://www.addtoany.com/share#url=http%3A%2F%2Fwww.blacklistednews.com%2FSnowden%3A_What_The_Wikileaks_Revelations_Show_Is_%22Reckless_Beyond_Words%22%2F57208%2F0%2F38%2F38%2FY%2FM.html&title=Snowden%3A What The Wikileaks Revelations Show Is "Reckless Beyond Words"]Share[/url] | Print This
[url=https://www.addtoany.com/share#url=http%3A%2F%2Fwww.blacklistednews.com%2FSnowden%3A_What_The_Wikileaks_Revelations_Show_Is_%22Reckless_Beyond_Words%22%2F57208%2F0%2F38%2F38%2FY%2FM.html&title=Snowden%3A What The Wikileaks Revelations Show Is "Reckless Beyond Words"]Share[/url]TwitterFacebookGoogle+StumbleUponEmailPinterestReddit
SOURCE: ZERO HEDGE
While it has been superficially covered by much of the press - and one can make the argument that what Julian Assange has revealed is more relevant to the US population, than constant and so far unconfirmed speculation that Trump is a puppet of Putin - the fallout from the Wikileaks' "Vault 7" release this morning of thousands of documents demonstrating the extent to which the CIA uses backdoors to hack smartphones, computer operating systems, messenger applications and internet-connected televisions, will be profound.
As evidence of this, the WSJ cites an intelligence source who said that "the revelations were far more significant than the leaks of Edward Snowden."
- Quote :
-
Mr. Snowden’s leaks revealed names of programs, companies that assist the NSA in surveillance and in some cases the targets of American spying. But the recent leak purports to contain highly technical details about how surveillance is carried out. That would make them far more revealing and useful to an adversary, this person said. In one sense, Mr. Snowden provided a briefing book on U.S. surveillance, but the CIA leaks could provide the blueprints. [size] Speaking of Snowden, the former NSA contractor-turned-whistleblower, who now appears to have a "parallel whisteblower" deep inside the "Deep State", i.e., the source of the Wikileaks data - also had some thoughts on today's CIA dump. In a series of tweets, Snowden notes that "what @Wikileaks has here is genuinely a big deal", and makes the following key observations "If you're writing about the CIA/@Wikileaks story, here's the big deal: first public evidence USG secretly paying to keep US software unsafe" and adds that "the CIA reports show the USG developing vulnerabilities in US products, then intentionally keeping the holes open. Reckless beyond words." He then asks rhetorically "Why is this dangerous?" and explains "Because until closed, any hacker can use the security hole the CIA left open to break into any iPhone in the world." His conclusion, one which many of the so-called conspiratorial bent would say was well-known long ago: "Evidence mounts showing CIA & FBI knew about catastrophic weaknesses in the most-used smartphones in America, but kept them open -- to spy." To which the increasingly prevalent response has become: "obviously." [/size] - Quote :
- 6h
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]PSA: This incorrectly implies CIA hacked these apps / encryption. But the docs show iOS/Android are what got hacked - a much bigger problem. https://twitter.com/wikileaks/status/839120909625606152 …[/ltr] - Quote :
Follow
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]Still working through the publication, but what @Wikileaks has here is genuinely a big deal. Looks authentic.[/ltr]
8:53 AM - 7 Mar 2017
7,0047,004 Retweets
9,3019,301 likes
- Quote :
- 6h
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]What makes this look real?
Program & office names, such as the JQJ (IOC) crypt series, are real. Only a cleared insider could know them.[/ltr] - Quote :
Follow
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]If you're writing about the CIA/@Wikileaks story, here's the big deal: first public evidence USG secretly paying to keep US software unsafe. pic.twitter.com/kYi0NC2mOp[/ltr]
9:37 AM - 7 Mar 2017
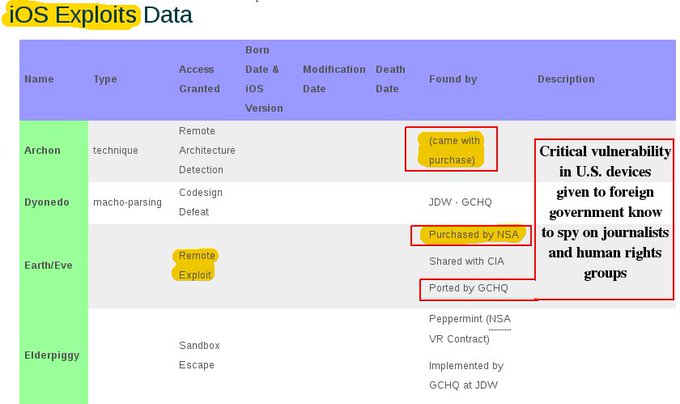
8,6908,690 Retweets
7,6887,688 likes
- Quote :
- 5h
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]If you're writing about the CIA/@Wikileaks story, here's the big deal: first public evidence USG secretly paying to keep US software unsafe. pic.twitter.com/kYi0NC2mOp[/ltr] - Quote :
Follow
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]The CIA reports show the USG developing vulnerabilities in US products, then intentionally keeping the holes open. Reckless beyond words.[/ltr]
9:49 AM - 7 Mar 2017
6,0526,052 Retweets
6,9406,940 likes
- Quote :
Follow
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]Why is this dangerous? Because until closed, any hacker can use the security hole the CIA left open to break into any iPhone in the world. https://twitter.com/Snowden/status/839171129331830784 …[/ltr]
9:55 AM - 7 Mar 2017
6,5636,563 Retweets
6,4526,452 likes
- Quote :
Follow
 Edward Snowden Edward Snowden
 @Snowden @Snowden
[ltr]Evidence mounts showing CIA & FBI knew about catastrophic weaknesses in the most-used smartphones in America, but kept them open -- to spy. https://twitter.com/wikileaks/status/839188928313851904 …[/ltr]
11:19 AM - 7 Mar 2017
6,6986,698 Retweets
6,4146,414 likes
[size] SHARE THIS ARTICLE...[/size] |
|





